Ransomware attacks are becoming a bigger problem every year. According to Chainalysis, confirmed Ransomware attacks grew by 10% in 2024, and more victims are listed on dark web extortion sites.1 This year also saw the largest ransom payment ever recorded, with about $75 million paid by a Fortune 50 company to the Russian-based Dark Angels Ransomware group.2
As these attacks increase in frequency and severity, should they be considered a form of terrorism that threatens our safety and security?

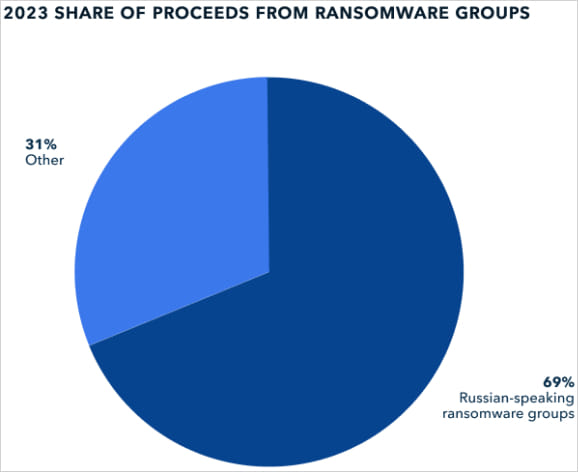
Russian Ransomware Groups Are Responsible For 69% Of All Ransom Payments
According to a report by TRM Labs, Russian-based Ransomware groups made at least 69% of all cryptocurrency proceeds from Ransomware, totaling over $500 million.
Source: TRM Labs
The report also shows that in 2023 alone, the biggest groups are all run by Russian-linked threat actors, including LockBit, Black Basta, ALPHV/BlackCat, Cl0p, PLAY, and Akira.
ALPHV/BlackCat has shut down, and LockBit’s activity has slowed after law enforcement disruptions. However, new groups like RansomHub are stepping in to become one of the most active Ransomware groups.
TRM reports that LockBit and ALPHV alone received at least $320 million in cryptocurrency ransom in 2023, with total Russian Ransomware proceeds exceeding $500 million.
Furthermore, the three biggest Russian dark web markets processed $1.4 billion in transactions, while Western markets only reached $100 million during the same time.
Source: TRM Labs
TRM reports that Russian-language darknet markets sell many illegal goods and services, making up 95% of all global sales of this type.
Senate Intelligence Committee to Declare Ransomware As Terrorism
The U.S. Justice Department enforced Ransomware investigations to the level of terrorism after the Colonial Pipeline attack in May 2021. A Senate Intelligence Committee proposal, led by Chairman Mark Warner, D-Va., aims to treat Ransomware as an official terrorist threat.
Part of the 2025 Intelligence Authorization Act, the bill labels Ransomware groups as “hostile foreign cyber actors” and targets countries that support them as “state sponsors of Ransomware.” It would allow sanctions and give the U.S. intelligence community more power to pursue these threats, making Ransomware a top national security priority.
According to the Intelligence Committee’s proposal, “foreign Ransomware organizations, and foreign affiliates associated with them, constitute hostile foreign cyber actors, that covered nations abet and benefit from the activities of these actors, and that such actors should be treated as hostile foreign cyber actors by the United States,” listing 18 Ransomware gangs, from DarkSide to Black Basta.
The bill cited LockBit; according to a report by Cyfirma, LockBit is no longer one of the top groups. REvil, another group, mostly stopped operating after Russian law enforcement targeted them in 2022.
The bill would make Ransomware a top focus for the U.S. intelligence community. It requires the Director of National Intelligence (DNI) to consider Ransomware threats to important infrastructure as a key part of national security.
The DNI would need to identify the most dangerous individuals and groups, where they operate, their methods, their connections to their countries, and any missing information that makes it hard to fight Ransomware.
The Limits Of Sanctions In Fighting Ransomware
Many countries that profit from Ransomware are already under US sanctions. For instance, North Korea, which faces international sanctions for its weapons programs, is unlikely to be deterred by additional sanctions. In fact, these sanctions may drive North Korea to rely more on cybercrime.
Critics of the bill also argue that sanctions are often ineffective against countries like Russia and China. Their strong economies can handle sanctions, and state entities may even use them to gain public support against those enforcing the sanctions. A study even indicates that “prosecuting these cybercriminals has proven exceedingly difficult” because these perpetrators are from nations that do not extradite criminals to the U.S.
We will see if the proposal is adopted and if it actually affects Ransomware groups and the governments that support them.
Do Not Pay That Ransom, According To Government Agencies
There are already U.S. government crackdowns against Ransomware. In November 2023, a White House statement announced a meeting in Washington, D.C., for representatives of the International Counter Ransomware Initiative (CRI).
The meeting, which included 48 countries, the European Union, and INTERPOL, focused on three main goals to address the growing threat of Cyberattacks and to agree on not paying ransoms. Key deliverables include developing capabilities, sharing information, and fighting back.
Indeed, Ransomware has become a serious national security issue. It affects not just big companies but also small businesses, with 51% of them paying the ransom when they get hit.
To also help fight this issue, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) strongly advise that businesses and individuals not pay the ransom. Paying doesn’t guarantee that the hackers will give back access to your files, and it only fuels more attacks.
If you are affected by Ransomware, the FBI encourages you to report it to their Internet Crime Complaint Center (IC3). The Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) also requires organizations to report cybercrime and Ransomware payments to CISA.
Reporting helps authorities understand the problem better and can lead to actions against the hackers. It’s important for everyone to work together to fight against Ransomware and keep our businesses and communities safe.
| Don’t let Ransomware disrupt your business like it did in this case study. This company faced huge costs, paying the attackers and losing $275,000 just in employee salaries while they were down for 71 days! They couldn’t sell anything because they had no inventory data. Protect your business by learning from their experience. |
FAQ
Is Ransomware Considered Terrorism?
The proposed 2025 Intelligence Authorization Act aims to classify Ransomware attacks as terrorist threats, recognizing their serious impact on society. By doing this, it focuses on placing stronger measures to combat these attacks and protect businesses and individuals.
What Is An Example Of Cyber Terrorism?
An example of cyber terrorism is the Colonial Pipeline. Hackers disrupted the pipeline’s operations, causing fuel shortages across the East Coast. The lack of detection, monitoring, and remediation measures allows attackers to stay hidden and penetrate the network. This attack showed how cyber threats can have serious effects on people’s lives and the economy.
How To Prevent Ransomware Attacks?
To prevent Ransomware attacks, start by doing due diligence, such as keeping software updated and training employees to recognize threats. It’s also helpful to create strong off-site and offline backups of your data. If you do experience an attack, 2Secure Corp advises contacting the FBI right away. Also, consider using a Ransomware attack simulation to test your defenses and improve your response plan.

Source:
- Chainalysis Team. (2024, August 15). Crime [Review of Crime]. 2024 Crypto Crime Mid-Year Update Part 1: Cybercrime Climbs as Exchange Thieves and Ransomware Attackers Grow Bolder. https://www.chainalysis.com/blog/2024-crypto-crime-mid-year-update-part-1/
- Zscaler: A Leader in the 2024 Gartner® Magic QuadrantTM for Security Service Edge (SSE). (2024). Zscaler.com. https://www.zscaler.com/campaign/threatlabz-Ransomware-report




