In this MSP Voice interview, Yigal Behar from 2Secure shares his journey in Cybersecurity, taking us from his beginnings in Israel to his work in the U.S. Yigal has been in IT for over 20 years, with a focus on security since 2000. He first ran a business in Israel, but as Cybersecurity evolved, he sold that company and shifted his career entirely to security.
He joked about how he used to read firewall manuals even in the bathroom to make the most of every moment—demonstrating his commitment to learning about the field from the start.
His early experience involved providing security consultancy for both private companies and government sectors, even working with high-profile clients like the Prime Minister’s office. Later, when he moved to America, Yigal used his background in enterprise security to create a Cybersecurity consultancy aimed at helping small businesses protect themselves.
When asked about his role, he explained that his company blends aspects of a Managed Security Service Provider (MSSP) and Managed Detection and Response (MDR). While MSSPs monitor security activities, MDRs like Yigal’s company go further by not only watching for threats but also acting to neutralize them when they occur.
Yigal tells MSP Voice, “So it depends with the customer how the engagement is. We are trying to accommodate the request, so let’s say [they] said, ‘Okay, just notify us what to do’—this is what we do. Yeah, if that’s [to] do the elimination, we do the renovation; however the customer wants, this is how we do it. Okay, kind of a combination, I would say.”
Advice For Managed Service Providers
In this part of the interview, Yigal advises Managed Service Providers (MSPs) who might not be focusing on Cybersecurity yet. He suggests they need to start working on Cybersecurity right away—saying, essentially, they should have started “yesterday.”
Yigal shares that he recently spoke with a business consultant who is trying to help MSPs understand Cybersecurity better. Many MSPs lack expertise in security and don’t know much about it. Unlike other IT services, Cybersecurity isn’t as simple as selling software or backup systems. It requires a deeper level of knowledge and expertise to handle properly.
Yigal explains that it takes a lot of work to get a Cybersecurity service up and running. He talked to a consultant who thought it was a great idea to offer Cybersecurity services, but there’s more to it than just a good idea. You need to secure contracts, get the right suppliers, and put all the necessary pieces in place. It takes months to build a team and reach a level where you can reliably offer these services to clients.
He also mentions that while people often talk about using AI and machine learning to solve Cybersecurity issues, it’s not as simple as it sounds. Yigal points out that AI is still being developed and needs to be trained, much like teaching a child.
For example, you have to teach the machine what a “broken” or “normal” situation looks like by showing examples. This process takes time, and it’s not something that will happen overnight.
Threat Hunting
MSP Voice then asks Yigal how systems can detect when something unusual happens.
The idea is that the system should understand the “steady state”—or the normal conditions—and then notice when something changes. If there’s a shift from that steady state, the system should send an alert, flagging the unusual activity.
MSP Voice wants to know if this approach to detecting threats makes sense or if Yigal sees it differently.
Yigal responds that just collecting data isn’t enough to catch all threats. You might collect data from devices, networks, and various sources, and some of it will look familiar and safe. But some data points won’t match anything you’ve seen before. When you come across those, you need someone with experience to look closer and decide if something strange is actually a problem.
He goes on to talk about threat hunting. This process focuses on finding threats that are unknown or don’t have a clear signature, like new types of ransomware. Known threats have specific “indicators of compromise” that security tools recognize and can shut down quickly. But unknown threats don’t have these markers, which makes them harder to identify. That’s where threat hunters step in. They analyze these unusual events to figure out if they pose a real danger. So, while detecting known threats is straightforward, the real challenge lies in finding the unknown ones.
Approach To Threat Hunting
MSP Voice asks Yigal how he approaches threat hunting. They want to know what steps he and his team take to find unknown threats. It’s a question about the methods and strategy Yigal uses to spot potential dangers that don’t have clear signs or signatures.
Yigal explains his approach to threat hunting by comparing it to a war game. He imagines himself as an attacker, thinking like a hacker trying to break into a company’s system. He considers the organization’s structure, security measures, and defenses, then tries to figure out ways to get in without being noticed.
The goal of this exercise is to spot any weak points in the system—places where an attacker might slip through. If he finds that a hacker could get in without detection, he and his team work on creating extra layers of security to catch such intrusions in the future. This “war game” approach helps them prepare for real threats by constantly strengthening their defenses.
MSP Security
For MSPs, Yigal implies that it’s challenging to handle all this on their own. They would need resources, time, and the right expertise to stay on top of these threats, and it’s not easy for them to manage everything themselves.
Yigal talks about how many MSPs claim to offer security but often only provide basic protections like firewalls, antivirus solutions, and spam filtering. He finds it amusing when MSPs list these general tools and call it “security,” because these are just the basics, not real security measures. For Yigal, true security includes more in-depth practices like penetration testing and verifying authentication processes, which show a serious approach.
To help MSPs improve, Yigal’s company offers a special program designed to support them in strengthening their security offerings. This program includes marketing help, benefits for joining, and even participation in calls with potential clients to help convert leads into customers. Through this approach, Yigal’s team assists MSPs in cross-selling and upselling security services, helping them provide true protection to their clients.
MSP Monitoring
MSP Voice then asks how MSPs monitor their security. Yigal jokes a bit, calling it a “loaded question,” but then gives a thoughtful answer. He explains that his company offers a special program for MSPs that includes security monitoring because he knows many MSPs struggle with providing strong security.
As part of this program, his team offers free services like a “permeability assessment.” This means they will scan the MSP’s network to check for any weaknesses or issues.
This service is offered for free because, if the MSP is secure, their customers will be safer too. He also points out that in recent months, there have been increasing attacks from Ransomware groups specifically targeting MSPs, so it’s important to make sure their systems are strong before they help others.
Top Hits
“What are some of the things that the MSP really needs to look out for what are some of your top hits for a premise piece?” MSP Voice asks Yigal.
Yigal notes that credentials are a big issue. MSPs should ensure that customers are using two-factor authentication (2FA) for better protection, which some companies like Kasaya and ConnectWise are already pushing for.
Changing security protocols, such as regularly updating passwords, also comes in handy. Yigal points out a common mistake among IT professionals: using an admin account for daily tasks. Admin accounts have high-level privileges, and they shouldn’t be used for everyday work. It’s important to have separate accounts—one for regular use and another for administrative tasks.
Patch management is another critical area, as well as changing default settings. Many companies fail to change default settings, leaving their systems vulnerable.
Firewalls are also a big concern—Yigal says that 99% of firewalls he audits are misconfigured, and if they’re not set up properly, they’re not doing their job. If a firewall isn’t effective, it might be better to remove it and focus on improving the system’s speed instead.
Working With MSPs
Yigal then talks about how his company is always ready to help people who are eager to improve their security. He emphasizes that they enjoy working with Managed Service Providers (MSPs) who truly care about their own security and the security of their customers.
He explains that their service is ongoing and available on a month-to-month basis, meaning MSPs can continue using it as long as they need. It’s a flexible arrangement that can adapt to their changing needs.
Offer To MSPs
Well, what about the MSP’s customers? Yigal explains that when they work with MSPs, the MSP takes the lead with their customers. The MSP decides what services its customers need and then resells those services.
Yigal’s company operates in the background, focusing strictly on security. They don’t want to interact directly with the customers unless the MSP asks for it. If that happens, the customer would get a percentage of the setup.
Yigal says that his company doesn’t get involved in the IT side of things like installing software or configuring systems. They leave that up to the MSP. Their main focus is on security, which is what they’re passionate about. If a customer or MSP has a security issue or question, Yigal’s company is happy to help, but they don’t deal with other IT tasks. They only step in when there’s a security concern.
Technology
Yigal shares that he has an interest in robotics. He notes that robotics involves many things, including the Internet of Things (IoT), which can have security concerns. He finds robotics to be a very interesting area to explore.
He also mentions that some people can get a bit scared when they see videos of robot dogs doing all sorts of impressive things. Yigal jokes that these videos can be a bit unsettling for some, but adds that the robots are so advanced, that it’s almost impossible to resist their ability to adapt and change.
He humorously references the idea that “resistance is futile,” hinting at how unstoppable technological progress can feel sometimes.
Humans Are The Weakest Link
“So what technologies are you most worried about?” MSP presses.
Yigal brushes off that he’s not worried about the technology itself, but more about humans. He believes that humans are the weakest link in any system. If people aren’t doing what they should, it doesn’t matter how advanced the technology is. He points out that humans create technology, so if they make mistakes or don’t act carefully, it can cause problems.
From a security perspective, Yigal says you can have all the technology in the world, but if someone makes a bad decision or clicks on something they shouldn’t, it can lead to a breach. He humorously comments that humans often rely on AI to think for them, because sometimes they feel machines can think better than they can.
Then, Yigal prepares for the “rapid fire” round, where he answers six quick questions:
- Apple or Android? He chooses Android.
- Mac, Linux, or Windows? He prefers Mac.
- Amazon, Azure, or something else? He goes with Azure.
- Local backups, cloud, or both? He says both.
- Should you always virtualize? He firmly says, Yes.
- Which is worse: printer support or vendor cold calls? He doesn’t answer directly, but this question is clearly a lighthearted one meant to get a quick reaction.
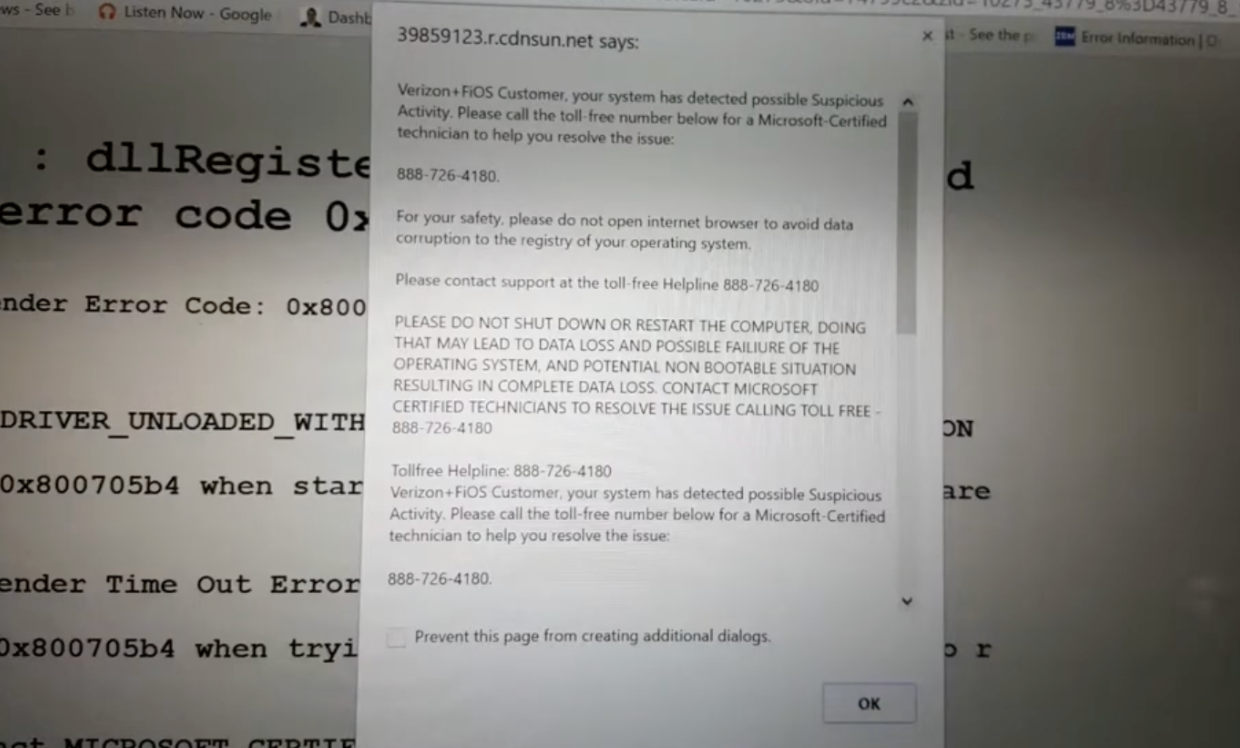
Yigal talks about how printers can be a security risk. He points out that printers, especially those connected to phone lines or modems, can be an attack surface for hackers. He shares an interesting fact: hackers have been known to target fax machines. He explains that these hackers can send certain commands to a fax machine, which opens it up and gives them access to the rest of the network.
This kind of vulnerability was discovered by a company called Checkpoint. Yigal finds it crazy that something as seemingly harmless as a phone line could be used for an attack. It’s a reminder that you have to think about security in unexpected places.
A Simple Guide To Security For Small Business Owners
Wrapping up, Yigal shares that if people are interested, they can go to his website and download his ebook, which is available in a PDF version. He mentions that he also has a printed version of the book.
He explains that the book he wrote is meant to help small business owners with their security needs, and he kept the language simple so it’s easy to understand. He even mentions that he’s working on a second book, which sounds like it’s going to be just as helpful.

Be sure to check out this episode of MSP Voice on YouTube! For more podcasts and webinars, visit The Cybersecurity Insider on YouTube, Apple Podcasts, and Spotify.