Is your business prepared for the devastating financial hit of a cyberattack?
In this episode of The Cybersecurity Insider podcast, host Yigal Behar welcomes his guest, Gordon Coyle, an insurance expert specializing in cybersecurity.

About Gordon
Gordon is the owner of The Coyle Group, an insurance agency specializing in business insurance. The agency works with businesses of all sizes and across various industries. Gordon shares that cyber insurance has become a major part of their offerings in recent years.
According to Gordon, they started slow but have become strong advocates for the importance of cyber insurance and educating businesses about its coverage and benefits in case of cyber attacks or breaches.
Gordon continues that his agency handles all types of business insurance, but cyber insurance is particularly important for new and existing clients. He proudly shares that his firm is a third-generation family business, started by his grandfather and his brother in 1929, and he has been in the insurance business for 40 years.
Intrigued, Yigal asks Gordon about the role of cyber insurance and security in the present time and why it has become so indispensable.
Why Is Cyber Insurance Needed
Gordon explains that cyber insurance is important today as it’s the only coverage that responds to breaches, hacks, attacks, or other cyber events where a business suffers losses related to digital assets.
If a company values its data, it makes sense to insure it. The most common threat they see is ransomware, and the incidence and cost of these threats are increasing exponentially.
Gordon believes every business, regardless of size, needs cyber insurance if they store data digitally, which he argues is the case for almost every company today. He isn’t just referring to e-commerce or online assets, but also everyday business operations like banking, customer information storage, and using software like QuickBooks. Unless a business operates entirely on paper and pencil, Gordon asserts they need cyber insurance.
The conversation takes a humorous turn as Yigal mentions fax machines and how some organizations, even the Internal Revenue Service (IRS) and insurance companies, still rely on them.
Yigal shares his own experience of having to get a fax machine to deal with a car insurance issue and wonders whether to get a regular or digital fax. They both agree that fax machines seem outdated in the modern world, yet some entities still use them. Yigal says that if you’re not using a fax machine, you might be lucky.
Types of Cybersecurity Insurance
Yigal transitions the conversation to types of cybersecurity insurance, recalling a recent discussion with Gordon where he was advised to get cyber insurance despite being a cybersecurity professional himself. Intrigued by this advice, Yigal asks Gordon about the different types of cyber insurance and why it’s necessary.
Gordon explains that there are two main ways to buy cyber insurance: as an endorsement of a business owner’s policy for smaller companies, or as a standalone policy.
Gordon doesn’t recommend adding cyber insurance as an endorsement to a business owner’s policy, finding it insufficient with low coverage limits. Instead, he advocates for standalone cyber insurance policies. He mentions that around 15 companies offer cyber insurance, including established names like Travelers, Chubb, and CNA, as well as newer managing general agencies with unique policy forms and services.
Gordon notes that these standalone cyber insurance policies are generally similar across the industry, covering both first-party and third-party risks. The differences lie in coverage limits, triggers, and terms and conditions. These details can be quite technical but the policies themselves are fairly consistent.
Shifting focus, Yigal addresses the misconception that businesses are unique from a hacker’s perspective. Hackers target data, regardless of the type of business, and even small businesses are vulnerable, especially if they’ve been breached before.”They think that they are different, but in terms of the hacker’s perspective, they [are] looking for the data, so you are not special. Any event, any business is not different from another because they want the data regardless of what you do.”
He cites a statistic suggesting that businesses breached in the past six months are likely to be breached again due to unresolved vulnerabilities. Yigal then asks Gordon what the average business owner should look for in cyber insurance.

The Importance of Cyber Insurance for Businesses
Gordon says the main question business owners without cyber insurance ask is, “Why do I need it?” He reiterates that if a business has valuable data, it’s susceptible to theft, corruption, or ransomware attacks, making cyber insurance necessary.
He says that some business owners may be overconfident in their backups, but warns that hackers have new strategies like threatening to expose data if a ransom isn’t paid, even if the backups are intact.
Gordon insists that cyber attacks have various costs: ransoms, data restoration, lawsuits, and damaged hardware. He questions whether businesses are willing to risk hundreds of thousands or millions of dollars in potential losses for not paying a relatively small premium. He uses the example of a small business with a $1500 annual premium versus much larger losses.
For larger companies, Gordon points out that premiums might be higher, but the risks are also much greater. Lost productivity due to downtime caused by a cyber attack can be extremely costly. Cyber insurance helps fund the recovery process, including paying ransoms, hiring forensic experts, and ensuring data is cleaned and secure. “You help protect your customers’ data. Why? Because the data is valuable, so insurance is just a mechanism of funding the recuperation, remediation, and recovery from an attack.”
Cyber Insurance for Data Protection
Yigal recognizes Gordon’s point about data’s value and the role of insurance in recovery. He then shares a recent news story from Israel about a hospital breach where hackers accessed seven million patient records and encrypted backups, noting that even backups can be compromised. He mentions the importance of segmentation and risk assessment in determining the effectiveness of backups.
Underwriting Processes for Cyber Insurance
Yigal then turns to how insurance companies determine premiums and assess risk. He recalls their previous conversation where Gordon mentioned that insurance companies mainly focus on understanding the risk. He asks Gordon how they assess this risk and what business owners can do to lower their risk and secure better premiums.
Gordon explains that the process has changed considerably in the past 18 months. Previously, insurance companies would quote and issue policies based on basic information like the number of employees, annual sales, and simple security measures.
Now, underwriting involves questions about multi-factor authentication, air-gapped backups, data security, and employee phishing training. This applies to both new buyers and renewals.
Gordon shares that he’s currently working on renewals for several clients who initially obtained cyber insurance policies based on simple questionnaires. Now, they’re facing much more extensive applications with numerous questions about their security practices.
Gordon empathizes with clients who find this frustrating but explains that cyber insurers have been hit hard by ransomware claims and need to ensure their clients are taking security seriously.
He further reveals that some insurance companies conduct remote perimeter scans to check for vulnerabilities and “want to make sure that the posture of the client matches their underwriting profile and that they’re not giving a policy or selling a policy to a client that doesn’t take security in a serious way.”
This includes looking for open ports, unpatched software, and other weaknesses. Yigal clarifies that these checks are done remotely, not on-site, and occur before the policy is even offered.
Yigal confirms that not all insurance companies do this, but some use it to assess and mitigate the risk before they agree to provide coverage. Yigal finds this practice interesting and realizes its value in helping insurance companies manage their potential liabilities.

Security Checks Is a Necessary ‘Intrusion’ for Risk Assessment
Gordon claims that some clients may find the security checks intrusive, questioning why the insurance company is examining their network. He draws a comparison to workers’ compensation insurance, explaining that in a large manufacturing firm, for instance, the insurance company would send an inspector to ensure the workplace is safe.
He explains that cyber insurance is a relatively new field, and insurance companies and underwriters are still learning how to assess and price the risks involved. New threats emerge daily, so they need ways to manage and price them accordingly. Gordon says that these scans are just one method insurance companies use to achieve this.
Yigal agrees with Gordon’s points, relating them to his background in Israel, where security is a top priority. He explains that the traditional concept of perimeter security, like a border checkpoint, is no longer sufficient. Information is everywhere, and a zero-trust approach is necessary, where verification precedes trust.
He then asks Gordon what a business owner needs to have in place before applying for cyber insurance. He shares his own experience of being asked detailed questions about contracts and security measures during the application process.
Yigal follows up by asking what happens if a business with insurance gets breached. He wonders if the insurance company will simply pay out the claim or investigate whether the business had the security measures they claimed to have in place when they applied for the policy. He questions whether the insurance company will ask for proof of policies, procedures, contracts, firewalls, and antivirus solutions before providing the funds.
Breach Coach in Cyber Insurance Claims
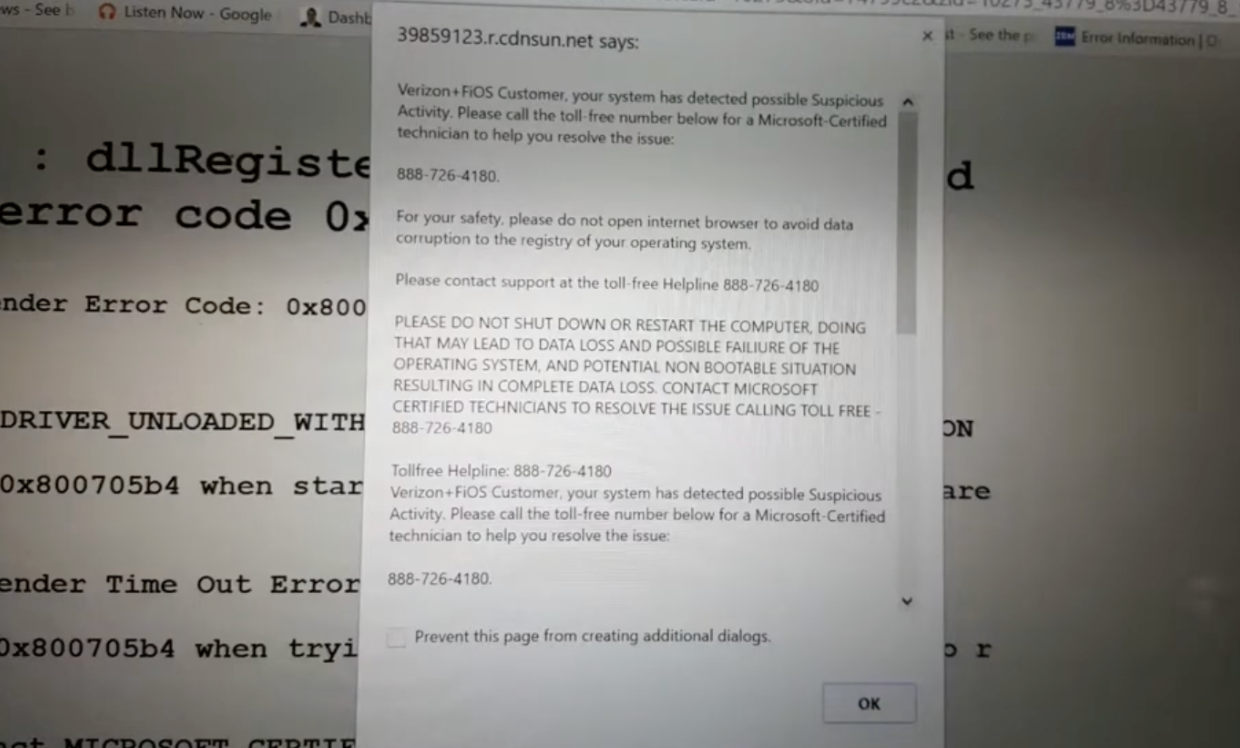
Gordon explains the typical process of a cyber insurance claim. He says that when a client gets hit with a ransomware attack, they usually call him in a panic. The first step is to call the insurance carrier’s 24/7 hotline, where a breach coach helps guide the client through the remediation process.
This person isn’t looking to deny coverage but rather wants to resolve the issue quickly, as every day that passes increases the cost of the claim.
Yigal finds this helpful to know, as it demonstrates the insurance company’s interest in getting the business back online quickly due to the business interruption coverage included in cyber insurance policies. Gordon shares a story about a prospect who suffered a ransomware attack before purchasing cyber insurance. They were out of business for 21 days and ultimately paid a $35,000 ransom.
The prospect initially thought they could resolve the issue themselves because they had backups, but the backups were also encrypted because they were stored on-site and not air-gapped. They tried working with their IT company, but it wasn’t equipped to handle the situation. The hackers even offered unsolicited advice to hire a new managed service provider, which shows how sophisticated and business-oriented hacking has become.
Cost of Downtime From a Ransomware Attack
Yigal jokingly shares his wife’s suggestion that he switch to the offensive side of cybersecurity because “you’re probably gonna make more money.” However, he personally prefers to focus on protecting clients.
Gordon agrees, noting that hacking has become a business in itself, with ransomware platforms operating as Software as a Service (SaaS) companies, making it easy and lucrative for hackers to exploit vulnerabilities.
Returning to the story of the prospect who experienced the ransomware attack, Yigal questions how much the 21-day downtime cost them. Gordon estimates the client’s revenue was around $15 million, and a quick calculation suggests the downtime could have cost them over $800,000 in lost revenue. Gordon emphasizes the significance of this loss, representing nearly a full month of work and a substantial portion of their annual revenue.
Yigal points out that the financial impact goes beyond lost revenue, as the company also had to pay the ransom and additional costs for remediation. He implies that the total financial damage from the attack likely amounted to tens of thousands of dollars beyond the lost revenue.
Obtaining Cyber Insurance After a Breach
Yigal wonders if the prospect who experienced the ransomware attack eventually got cyber insurance. Gordon admits they are still trying to obtain insurance, but it’s a difficult process since they’ve already been breached. This raises a major red flag for insurance companies, making it harder to get coverage after the fact.
Gordon compares it to trying to close the barn door after the cow has escaped. He maintains that the client was a victim, but also argues that they were a victim of their own inaction, either due to not understanding the risks or choosing to ignore them.
He clarifies that he isn’t blaming the client, as it’s possible they knew the risks but decided not to pay for insurance. Yigal then interrupts to share a similar story.

High Price of Ignoring Cybersecurity
Yigal shares a story of a customer who balked at paying a relatively small amount for cybersecurity services but ended up facing a much larger financial burden after a breach. He questions the logic behind such decisions.
Gordon explains that many business owners haven’t experienced a cyber attack, so they don’t believe it will happen to them. He adds that in the past, cyber attacks were primarily focused on stealing and selling data, but the game changed with ransomware, which offers hackers a much quicker and easier way to profit.
Returning to the prospect who suffered the ransomware attack, Gordon points out that getting cyber insurance now would be more difficult and expensive due to their increased risk. “You’re going to buy more, it’s going to be surcharged, there’s no doubt about that, and rightly so. You present a higher risk, um, and you need to clean up your act and have everything as bulletproof as possible, where you’re not going to even get a quote, or you’ll get a quote, but then once they do underwriting, they’re not going to sell you the policy.”
He then brings up a key element they haven’t yet discussed: reputational damage. This is another consequential cost associated with cyber attacks that businesses need to consider.
Reputational Damage Due To a Data Breach
Gordon shifts the conversation to reputational damage, citing the example of a law firm whose clients lose trust and business after a data breach. Cyber insurance policies often include a sub-limit for reputational damages that cover income loss due to client attrition. This coverage is particularly important for professionals like lawyers and accountants who rely heavily on trust.
Yigal agrees and stresses the often-overlooked value of reputational damage. He points out that it’s difficult to quantify the financial impact, as it involves not only lost customers but also prospective business due to negative word-of-mouth.
False Security In The Cloud
According to Yigal, no business is entirely safe from cyber threats. He recounts conversations with vendors who claimed their cloud services were highly secure, but he questioned their confidence given the high-profile breaches of companies like the FBI, Qualys, Microsoft, and FireEye. He even asked one vendor if he could get their service without using the cloud, preferring on-premise management to avoid cloud risks.
Gordon agrees that many clients have a false sense of security and believe they know everything they need to know. However, they often lack the specialized knowledge of cybersecurity professionals and insurance experts.
Gordon believes the best business owners are those who know their limitations and seek guidance from external experts to fill their knowledge gaps. This, he suggests, is a major challenge to overcome when selling services or insurance to potential clients.
The Impact Of Simple Security Measures
Yigal shares a story about a software company for the Jewelry industry that underwent a risk assessment. The results weren’t ideal as they show vulnerabilities in their hosting environment.
Yigal, able to see the systems of other customers on the same hosting platform, recommended the company move to a private cloud. Soon after the migration, the hosting company was hit with a ransomware attack. The software company’s CTO expressed gratitude to Yigal for the advice, as it saved them from utmost harm.
Yigal notes that even simple security measures, like patching vulnerabilities, can make a big difference. It doesn’t always require complicated solutions to improve security. “Just, you know, the low-hanging fruit; you can come and collect them and make sure that they’re not going to fall on the ground for anybody to come and pick them up.”
Choosing the Right Cyber Insurance
Yigal transitions to discussing what business owners should look for when selecting cyber insurance.
Gordon advises that the first step is to work with a cyber security insurance expert, especially for businesses with more complex needs. A generalist might be suitable for a small retailer, but a larger company with more employees and revenue needs an expert who understands the intricacies of cyber insurance policies and can guide them through the process.
Gordon asserts that an expert can help business owners understand the coverage and exclusions of different policies, as well as the value-added services offered by various providers. These services might include employee phishing training, network scans, and other cybersecurity measures. He believes the expert’s advice is necessary in choosing the right policy for a business’s specific needs.
Yigal agrees and draws a parallel to healthcare, explaining that a general doctor might refer a patient to a specialist for eye problems. Similarly, a business owner should seek out an expert in cyber insurance to get the most appropriate coverage and guidance.
Yigal recalls a recent conversation with a potential customer who expressed a desire to work with separate IT and cybersecurity providers, viewing IT professionals as general practitioners and cybersecurity experts as specialists.

Costs & Coverage
Yigal then asks Gordon about the cost of cyber insurance policies. Gordon explains that it’s difficult to provide an exact figure, but for very small companies, minimum premiums typically start around $1200-$1500 per year.
For slightly larger firms, the range is likely between $2500 and $5500 annually, with the price increasing from there based on the coverage and size of the company.
Gordon notes that many companies opt for $1 million limit policies, but this may be insufficient for their actual needs. He highlights that most cyber policies have a $250,000 limit for cybercrime, which includes social engineering and fraudulent fund transfers. He suggests that companies with considerable exposure to these risks, such as law firms handling real estate transactions, may need additional coverage. He adds, “A million-dollar limit may be sufficient; it may be totally fine for a small company, but, you know, a 100 million-dollar sales company probably should be buying five to ten million dollars a year.”
Cyber Insurance Limits
Gordon discusses a trend where customers are increasingly demanding higher limits of cyber insurance coverage. He mentions a call he had where a vendor required $5 million in cyber insurance, a significant increase from the typical $1 million limit just a year ago. This demand for higher limits can be attributed to several factors, including peer benchmarking and industry trends.
But, obtaining such high limits is becoming more challenging, as many cyber insurance companies are limiting their exposure due to the rising number of claims. To meet the higher demands, businesses often need to purchase a combination of primary and excess cyber policies. The primary policy covers the initial amount, and the excess policy covers any remaining amount up to the desired limit.
Yigal confirms that it’s indeed possible to get multiple policies from different companies, but Gordon says to coordinate these policies in a primary and excess structure. Having multiple primary policies can lead to conflicts and delays in claim payouts due to the “other insurance” condition, where each insurer tries to avoid paying first.
Gordon recommends arranging the policies in a tower of coverage, where each insurer understands their position in the hierarchy. This ensures that the primary insurer pays first, followed by the excess insurers in their designated order.
Two “Buckets” of Cyber Insurance Benefits
Gordon shares a story about a West Coast client who called him at 3 a.m. in a panic, suspecting a security breach in their credit card processing system. Fortunately, the client remembered their cyber insurance policy and called the 24/7 claims hotline. The next morning, the client expressed gratitude for the policy, relieved to have immediate access to expertise and resources to help them recover from the potential financial loss.
According to Gordon, cyber insurance provides two key things: a “bucket of resources” (expertise and guidance) and a “bucket of money” (financial assistance for recovery). He explains that the expertise helps businesses understand and respond to the threat, while the money covers expenses like hiring forensic experts, lawyers, and public relations firms, as well as costs related to business interruption, stolen money, and damaged hardware/software.
Overlooked Vulnerabilities
Gordon offers another example of an international company whose European coverage didn’t extend to the U.S. During the insurance process, a scan displayed huge security exposures that the client was unaware of. This discovery led to the company taking immediate action to fix the vulnerabilities, showcasing the value of cyber insurance even before a claim is made.
Yigal expresses his surprise that such a large company with external security resources hasn’t identified these issues. He draws a parallel to the recent Java Apache Log4j vulnerability and notes the common issue of companies not knowing their inventory or systems well enough.
The company uses SaaS solutions like Salesforce, which the business owner has no direct control of and is at the mercy of the provider’s security practices. “Apparently Salesforce are using raw4j and are also vulnerable,” Yigal states.
Yigal finds this situation very bothersome and believes others would feel the same if they thought about it.
Yigal expresses his skepticism about the cloud, recalling an email from 15 years ago predicting the obsolescence of IT professionals due to the rise of the cloud. He questions the location and security of data stored in the cloud and notes that many people don’t understand the concept.
Yigal then concludes episode 24 of The Cybersecurity Insider podcast, thanking Gordon Coyle for his expertise and insights on cyber insurance.
For more upcoming discussions on vulnerabilities, exploits, ransomware attacks, and other critical security incidents, tune in to The Cybersecurity Insider podcast. Stay informed with our latest episodes, available on YouTube, Apple Podcasts, and Spotify.
This time we had Gordon Coyle our Cybersecurity insurance expert talking about … secu err no Insurance policies for Cyber incidents.
What to look for and how to shop for the best policy.