Have you ever wondered about the devastating impact of network breaches on businesses? On this episode of The Cybersecurity Insider podcast, host Yigal Behar dissects a real-world case study.
He discloses how a network breach unfolded, exposes the vulnerabilities that hackers exploited, and shares the critical lessons learned from this incident.

History
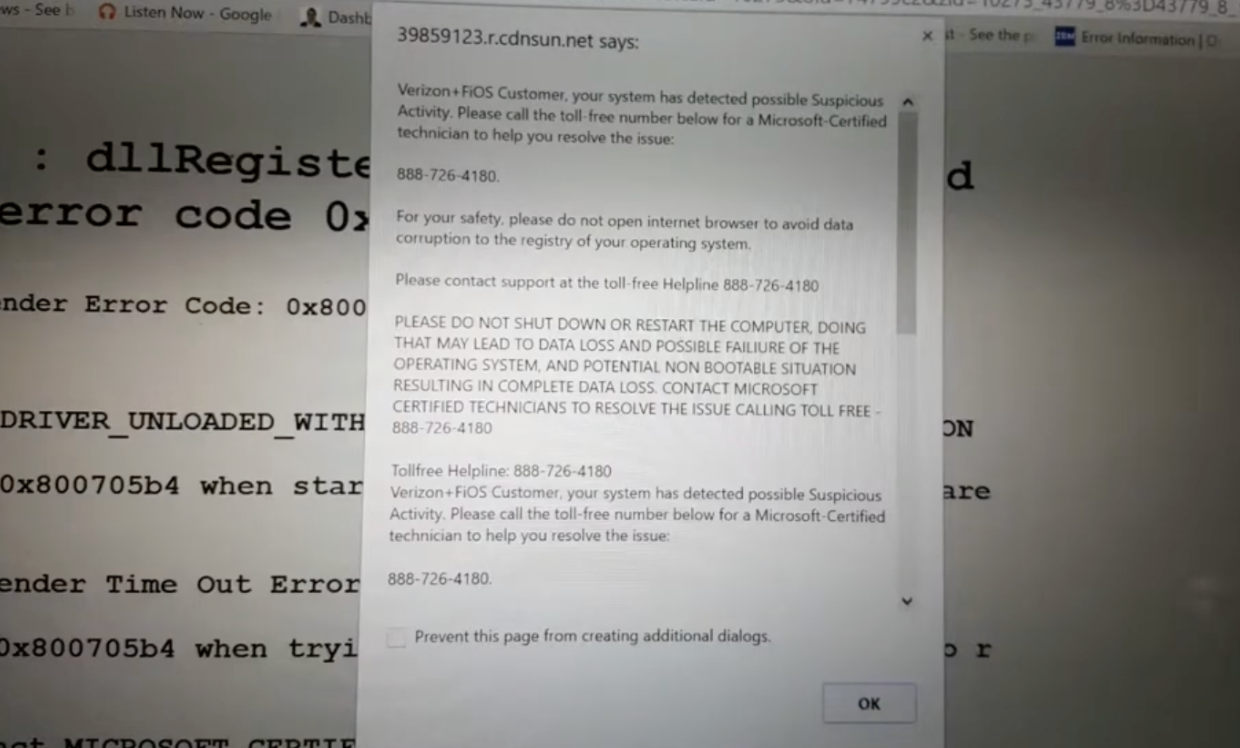
Yigal starts with a case study involving a customer who experienced a breach in their Office 365 system. The customer received a fraudulent invoice for $30,000, which prompted an investigation. After two months, Yigal and his team discovered vulnerabilities in the company’s Office 365, computer network, and employees’ home computers.
Yigal recounts his history with the customer, starting in 2017 when he advised them to implement network monitoring. A year later, the company contacted Yigal after an employee’s actions cost them a significant amount of money. This incident led to delays and additional expenses related to a Salesforce implementation.
Investigation
Yigal and his team investigated the employee’s workstation and found inappropriate use of company resources, such as using a dark web browser, accessing email services not related to work, and hosting a website for a personal business. Two months later, the company contacted Yigal again due to an Office 365 breach.
Two Events
Yigal points out that since 2017, the customer has experienced two major events. The first event was an insider threat that resulted in a high cost for the company.
The second event involved CEO fraud, where the attackers observed the company’s invoice approval process. They then sent invoices impersonating someone from within the company, using old signatures and logging into portal.office.com. The attackers sent two invoices, one for $30,000 and another for $150,000.
Other Problems
Yigal informed the customer about additional problems found within their network. During the investigation, they discovered dark web actors attempting to access an SSH server set up by the customer to receive Salesforce information. Yigal alerted the customer early on, stating that someone would eventually gain access to the server.
They identified two main issues with the setup. First, the SSH server was located on the internal network, behind the firewall, instead of in a DMZ (demilitarized zone). Second, the data flow was not controlled properly, as they were pushing data from the SSH server to the outside instead of pulling it from the inside. This lack of control allowed unauthorized access and potential data breaches.
Office 365 Authentication
Yigal and his team also discovered that the company was using weak authentication methods for Office 365, relying on SMS instead of the more secure Microsoft Authenticator app. They advised the customer to switch to the app to enhance security.
Another significant issue was the presence of mixed roles. The person managing Office 365 was using a global admin role along with their personal email address for the account. This meant that if the email address was compromised, the attacker would gain admin rights to the entire Office 365 installation. Yigal advised separating admin roles from personal email accounts.
Furthermore, they found instances of multiple logins from various locations, indicating potential unauthorized access.

Smoking Gun
After finding these issues, the customer questioned Yigal about the lack of a definitive “smoking gun” to identify the culprit behind the breach. Yigal explained that it was difficult to pinpoint the exact source due to everyone working from home at the time of the incident.
He mentioned that the user responsible for the breach could have used their personal home computer, a friend’s device, or even public Wi-Fi, making it impossible to trace without access or visibility to those devices.
iPhone VoIP
Later on, Yigal discusses a new development with the customer, who is considering adding iPhone VoIP to their system. The VoIP provider suggests bypassing the company’s firewall and connecting their box directly to the internal network, with a public IP address. Yigal raises concerns about this approach, as it bypasses existing security measures and exposes the network to potential threats.
Yigal questions the provider’s ability to guarantee the security of their box and expresses concerns that dark web actors, previously targeting the SSH server, will now shift their attention to this new vulnerability. “I said, ‘Can you give me any kind of assurance that your box is going to be safe and nobody will be able to penetrate that box?’ Because I told the customer, you know, ‘Once you have this box in parallel, we know now that those dark web actors will now go after that box as well.'”
Yigal asserts that it doesn’t take a security expert to predict the potential consequences of the VoIP provider’s proposed setup. He warns that if attackers successfully penetrate the VoIP box, they could easily gain access to the entire network by changing settings on the LAN.
The customer eventually agrees to connect only the phones to the network, not the VoIP box, as long as the existing firewall can manage quality of service and bandwidth allocation for the phones. Yigal assures them that this is possible and cites other installations as examples.
Yigal then introduces additional recommendations, such as implementing a backup system for Salesforce information and conducting a risk assessment. However, the customer seems unmoved by these findings and recommendations, not viewing them as issues or “smoking guns.”
Aversion to Security Measures
In a previous conversation, the current CTO suggested using Malwarebytes for protection, but Yigal disagreed, stating that it wouldn’t be sufficient. He argued that Malwarebytes and similar solutions cannot detect advanced threats like lateral movement within the network using tools like RDP, PowerShell, or PsExec. Yigal recommended a more advanced monitoring solution, but the customer was hesitant due to the increased cost.
Despite Yigal’s warnings and recommendations, the customer rejected all his suggestions. Yigal documented everything in a closing letter that indicated the increased exposure and risks involved in their decision. According to him, the customer wasn’t receptive to his advice.
Yigal ends the podcast by thanking the audience for watching and urging them to avoid similar mistakes. He urges viewers to invest in proper web application security measures to protect data, employees, software, and their overall business.
Watch The Cybersecurity Insider podcast for more cybersecurity tips and best practices. You can also catch us on YouTube, Apple, and Spotify.